Penetration Testing
Cocha will simulate a real-world cyberattack against your computer system to evaluate the security of the system, identify vulnerabilities, and develop an effective defense.
Get Your Free Security Review
Complete Cocha’s online cybersecurity questionnaire today and see how safe your organization’s data is.

Penetration Testing
Cocha provides penetration testing and vulnerability assessments leveraging advanced tools and approaches to discover “holes” in your systems, networks and applications.
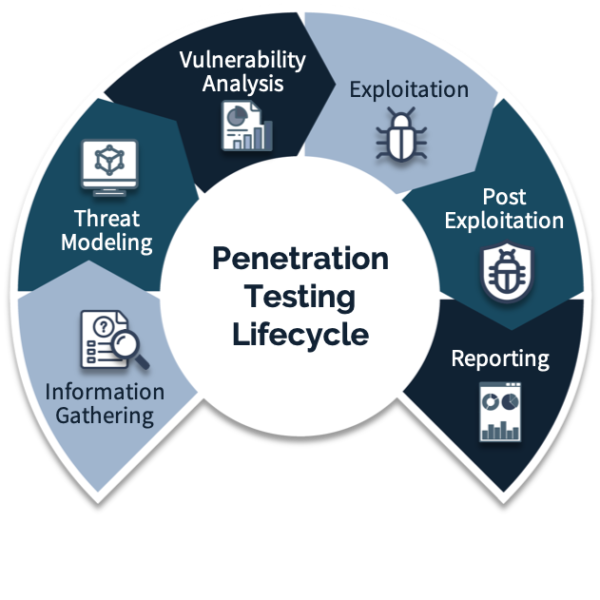
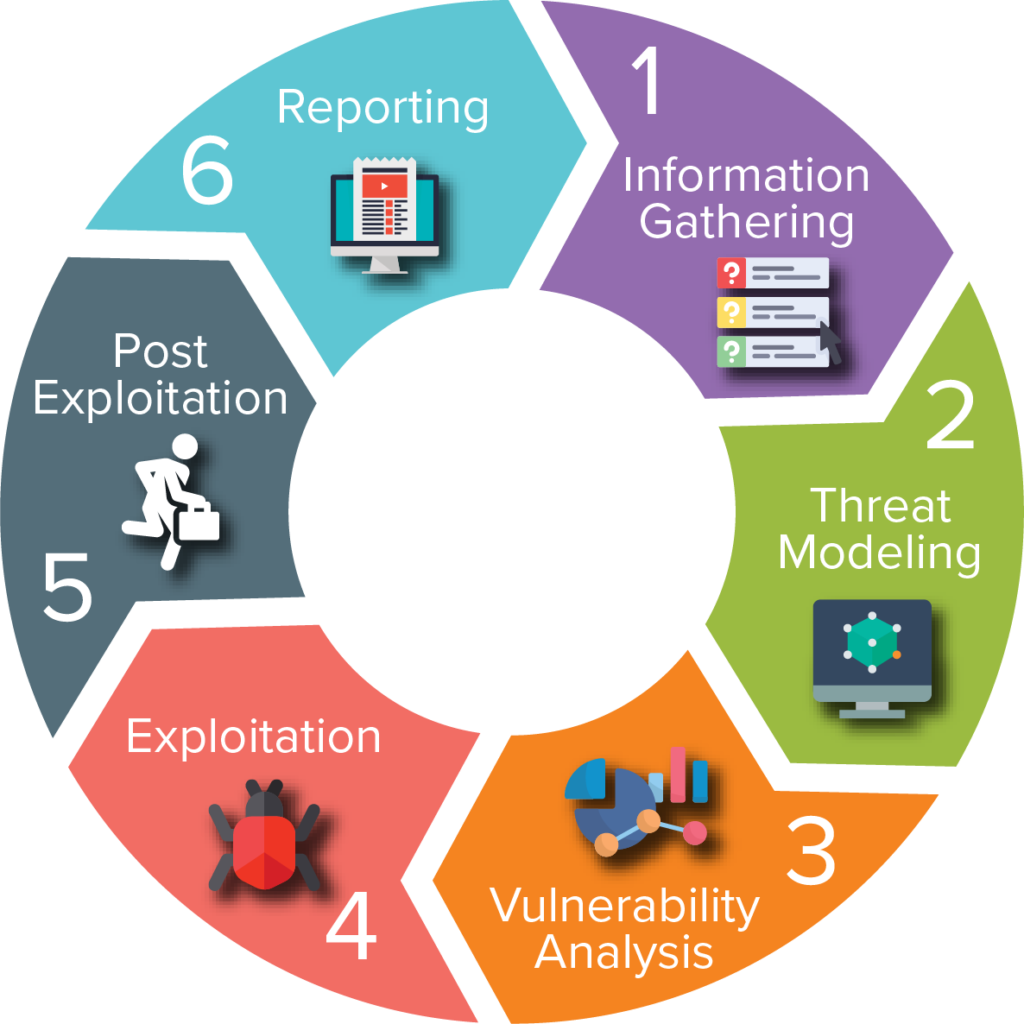
Penetration testing involves testing the security of an organization’s computer systems, networks, or web applications by simulating a cyber-attack. The goal of the test is to identify vulnerabilities in the systems and provide recommendations for improving the security posture.
Overview of Services
Cocha’s approach to providing penetration testing includes the following elements:
- Scoping and Planning: This involves defining the scope of the test, including which systems will be tested, what types of tests will be performed, and what objectives the test will accomplish.
- Vulnerability Assessment: This involves using automated tools and manual techniques to identify potential vulnerabilities in the systems being tested.
- Exploitation: This involves attempting to exploit the vulnerabilities found in the previous step to gain access to sensitive information or systems.
- Reporting: This involves documenting the findings of the penetration test and providing recommendations for remediation of any vulnerabilities found.
- Retesting: This involves conducting follow-up testing to ensure that any vulnerabilities identified during the initial testing have been properly addressed.
Some additional services that may be included in a penetration testing service offering include social engineering testing, wireless network testing, and physical security testing.
It’s worth noting that penetration testing is just one aspect of a comprehensive security program. To ensure the security of an organization’s systems, it’s important to also have measures in place to prevent and detect attacks, such as firewalls, intrusion detection systems, and security monitoring. Cocha can help with all these needs as well.